Internet Security
Internet Security. Use of the guide. Aim This presentation is prepared to support and give a general overview of the ‘Internet Security’ Guide and should be read in conjunction with the publication. Use of the Guide
Share Presentation
Embed Code
Link
Download Presentation
- security
- computer systems
- internet security
- web server
- corporate computer systems
- advanced systems high availability

eitan + Follow
Download Presentation
Internet Security
An Image/Link below is provided (as is) to download presentation Download Policy: Content on the Website is provided to you AS IS for your information and personal use and may not be sold / licensed / shared on other websites without getting consent from its author. Content is provided to you AS IS for your information and personal use only. Download presentation by click this link. While downloading, if for some reason you are not able to download a presentation, the publisher may have deleted the file from their server. During download, if you can't get a presentation, the file might be deleted by the publisher.
Presentation Transcript
- Internet Security
- Use of the guide Aim This presentation is prepared to support and give a general overview of the ‘Internet Security’ Guide and should be read in conjunction with the publication. Use of the Guide • This guide aims to take the reader form a general understanding of computers and networking to an understanding of the issues and risks involved in Internet security by: • presenting the potential risks of using unsecured computer systems to intentionally spread fear, uncertainty and doubt at the outset. • defining Internet security, which also encompasses Information security in an overall holistic approach. • giving an overview of current legislation that any company dealing with information/data on computer systems must take into account. • discussing some of the ways in which your computer systems can be compromised. • giving best practice recommendations to protect your computer systems.
- Fear uncertainty and doubt • 80% of attacks against corporate computer systems come from inside the organisation. • Remaining 20% of attacks come from the Internet or over the organisation’s WAN. • Not all attacks are carried out by a real live hacker - across the Internet automated systems scan web sites and continually check for known vulnerabilities. • Two major threats to an Internet connected system are the computer virus and the Trojan program. • Default – ‘out of the box’ - installations of popular email, word processing and web server programs are rarely safe from exploitation by malicious users. • There are solutions for such attacks but someone has to be tasked with keeping up with the latest information.
- Internet Security What is Internet Security • It is the application of security to computer systems that specifically provide connections to, connectivity across or services to, the Internet. • First building block is perimeter security. • Computers providing services over the Internet require special attention to repair any bugs or close any known loopholes in the software they are running, i.e. hardening. • Taking a holistic approach, the protection of your information from loss or corruption must also be considered. • Important to undertake certain tasks to protect data. • Must consider all aspects of access to computer data when thinking of information security • People and processes within your company must be an integral part of your security.
- Current legislation • Any company dealing with data on computers must take into account the following legislation: Data protection • Intended to regulate organisations that determine the purposes for which and the manner in which personal data relating to living individuals are processed. Regulation of Investigatory Powers Act 2000 (“RIPA”) • Provides for the interception of communications and surveillance. Computer Misuse Act 1990 • Identifies specific criminal offences for unauthorised access to computers Common Law • Confidential information • Common Law Confidentiality • Non-disclosure Agreements
- Recognising the risks • A breach in security is potentially damaging for your business. • Some common ways of your computer systems being compromised is: Denial of Service • Tying up your computer resources with the hacker’s tasks - preventing your tasks from running properly. Accessing data • Bugs in software that allow it to operate in an unpredictable manner then they make the software vulnerable to hackers. Watching your every move • Programs that allow a remote user to control your computer - they can also report your activities back to the remote user. Vulnerable Internet gateways • By leaving holes in your perimeter security a hacker will know how to make best use of them. Vulnerable servers • Loosely secure OSs can be exploited by an unscrupulous internal user, as well as making the job of a hacker much easier.
- Best practice recommendations Holistic Computer Security • A way of approaching the security of your systems so that nothing is missed: • from the centre of your network to the end user, whether they are in your office or connecting from a remote site across the Internet. • In the same way that ISO 17799 looks at information security for the whole organisation starting at board level, holistic computer security starts from the same premise.
- Best practice recommendations Deny all unless specifically allowed • When developing a security policy from scratch, the simplest place to start is the premise 'deny all unless specifically allowed'. • Your default policy is completed once all computer systems on the network are correctly configured and operating with this bare minimum of allowed network traffic.
- Best practice recommendations Staff • The human factor is most important in the assessment of Internet security, as without the computer users, the computers are almost useless. • A culture of security can be created by including training about Internet security in the staff induction process with further awareness programs regularly provided to remind staff of its importance.
- Best practice recommendations Network Perimeter protection • The main protection for your internal systems, when connected to the Internet, is a firewall. • It is important to keep your exposure to the Internet to a minimum.
- Best practice recommendations Email security • Email has become a business critical communications tool and is the most common client application that companies use on the Internet. • It presents a potential risk to the business through the introduction of viruses, legal defamation or the distribution of other unpleasant and unwanted materials. • Protection must be provided against such unwanted email content.
- Best practice recommendations Web security • Browsing of the WWW is usually checked both for suitability of the site being browsed to prevent personal browsing of the web in company time, and to limit browsing to sites known not to be offensive. • Any security policy or computer use policy will define what the company deems to be suitable use.
- Best practice recommendations e-Commerce • e-Commerce is the basic practice of allowing commercial trading over the web. • Much of operating an e-Commerce site is really described in all the best practice recommendations presented within this guide. • There is no separation between actions taken to secure an internal server or a live e-Commerce web server.
- Best practice recommendations Remote access • Modems built in to individual machines must be part of the internal security audit. • Where dial in access is required for remote users, care must be taken to restrict both access to the dial in modem itself and also that the remote user’s access is restricted only to those systems actually required.
- Best practice recommendations Virtual Private Networks • Remote access is usually provided over the Internet in the form of a VPN. • VPNs are particularly useful in building a WAN between remote offices or partner companies. • The use of SSL encryption is common when you need to pass sensitive information to a web server, i.e. e-Commerce.
- Best practice recommendations Strong authentication • Strong authentication ranges from biometric checks to encrypted smart cards or two-factor authentication. • For local access to the machine, fingerprint or smartcard authentication is common and prevents password guessing. • For remote connections over a VPN, two factor authentication is usual, i.e. username and password supplemented by a computer generated pass code.
- Best practice recommendations Encryption • By encrypting a file you hide its contents from anyone that does not have the key to decrypt it. • Encryption systems are based at the file system level, i.e.information is stored encrypted without the applications having to be adapted. • When someone accesses a database record, file or email attachment they must also have the decryption key in order to view the contents.
- Best practice recommendations Security audit your servers • Inside the firewall, your public facing servers will be half-way house between the Internet and the internal networks of your organisation. • Operating systems and COTS software installed straight out of the box are rarely secure against attack. • Common vulnerabilities in operating systems can be exploited by a knowledgeable intruder. • Important to consider security holistically and pay attention to every part of the system.
- Best practice recommendations Backup/restore • Keeping your data safe starts with keeping a copy that is known to be recent and accurate. • When deciding what data to keep a backup of think of rebuilding the computer from scratch. • Practicing the process of restoring your systems several times with equipment of your own is a very valuable experiment.
- Best practice recommendations Advanced systems: Intrusion detection systems • Uncertainties in software engineering often allow a computer system to do things that the developers had not anticipated. • As traffic crosses the network between computers, IDS compares the communication between software applications against an up to date list of known holes, backdoors, etc. • Where a computer is seen to be attempting something outside the usual, safe, operations the network communication can be terminated.
- Best practice recommendations Advanced systems: High availability • To run a 24x7x365 operation on the Internet will eventually require a backup or fail over system for when the primary systems fail whether due to hardware or software malfunction. • Tricky part is that the backup systems should take over seamlessly and automatically from the failed primary systems • Any systems that provide security for your information should be considered as high risk.
- Best practice recommendations Advanced systems: Logging and computer forensics • Modern operating systems can keep logs of user accesses, administrator logons and actions, who has used a certain file, etc. • Two important prerequisites to this information being useful: • that all servers keeping log information have their clocks synchronised • that the log information is kept or backup up somewhere centrally.
- Best practice recommendations Advanced systems: Rollback • Rollback is structured way of restoring data from a known good backup, but ensuring that the computer systems being restored are all synchronised on the time line. • To ensure that rollback is possible, you must test your system. • Live test of logging, backup and restore will improve your confidence in the system and give you many clues as how best to automate the process, either using people or software.
- Best practice recommendations Advanced systems: ISO17799 • This top level down approach (management processes) is more likely to succeed than many other approaches. • Recognises need for top level commitment to ensure company has desire and motivation to undertake such a project - through top level commitment come the resources and funding to achieve success. • Without board-level buy-in, a successful implementation is very difficult to achieve.
- Best practice recommendations Advanced systems: Serviced security systems • As with most highly technical systems, often best to get someone who knows the full story to give you advice. • Services available range from security audits of your system on site/ from the Internet, to fully managing your complete security systems. • Remember: security is a process, not a product.
- Conclusion • Internet security is as important as insuring your computers against theft or damage in minimising loss and disruption. • Internet security is a very broad subject. • Along with the issues discussed in this document, there are other considerations to complete a provably secure computer system. • Assessment by a third party company is usually the minimum requirement for testing a security system. • Penetration testing by white hat hackers should be the basic requirements. • ISO17799 audits are an internationally recognised level of security audit - may even qualify for cheaper liability insurance from a specialist insurer. • All of the actions from the best practice sections would be discussed with you by a reputable security company. • An holistic approach to the application of Internet security will allow you to address all of the security loopholes.

Internet Security
Internet Security By Abdiasis Mohamud What is Internet Security Internet security is the practice of protecting and preserving private resources and information on the Internet.
781 views • 10 slides

Internet Security
Internet Security Why it’s important for you! Spam Spam - Unsolicited "junk" e-mail sent to large numbers of people to promote products, services, pornography, scams, nonsense, etc.
782 views • 35 slides

Internet Security
Internet Security. Protecting your Business Online. Benefits of the Internet for Businesses:. Conduct electronic commerce Provide Customer Service Collaborate with Partners Reduce Communication Costs Improve Internal Communications Access Information Rapidly.
338 views • 11 slides

Internet Security
Internet Security. Jon Lutz FSU College of Law Research Center Fall 2011. Antivirus . Free for Windows AVIRA http:// www.avira.com/en/avira-free-antivirus AVG http:// free.avg.com/us-en/homepage Avast http:// www.avast.com/en-us/index
835 views • 61 slides

Internet Security
Internet Security. You Just “Gotta” See. Simple talk is not enough when it comes to safe Internet practices. For schools , the point is that to ensure safe Internet access, teachers and other staff members must be actively involved in what students are doing on the Internet. . t ext .
295 views • 12 slides

Internet Security
Internet Security. Kamehameha Schools Kapalama High School Ke Ko’i Lipi 1 to 1 Laptop Learning Program Parent Presentation. Objectives. Discuss the Core Internet Securities Define common threats to your online security Offer options for being more secure online
428 views • 15 slides

Internet security
Internet security. Are Our Compliance Regulations Falling Behind. In the beginning. New security threats were introduced at each stage of the Web’s growth as previous threats were not always addressed. The Web inherits all of the Internet’s security vulnerabilities .
393 views • 21 slides

Internet Security
Internet Security. Why Internet Security?. to protect Web sites and other electronic files from attack by hackers and viruses. . Different Types of Virus. Spyware Adware Embedded Programs Trojan Horse Browser Hijackers Dialers Malware. Why do people make Virus? . Profit A challenge
341 views • 20 slides

Internet Security
Internet Security. Passwords. What Are Passwords?. September 2008: Hacker steals password, breaks into Vice-Presidential candidate Sarah Palin’s email account. 2005: Hacker steals file with customer passwords from advertising company Acxiom.
454 views • 34 slides

Internet Security
Internet Security. Sean Nagelski , Kristina Klima, and Kelly Sipko. Internet Security. Establish rules and measure to use against attacks over the Internet Privacy Settings Firewalls. Schools. Pros: . Cons:. Kids stay focused Safety Learn how to use academic search engines.
467 views • 13 slides

Internet Security
Internet Security. By Phillip Dinh 1301 Spring 2007 University of Houston. Map Slide. Slide 1: Title Slide Slide 2: Map Slide Slide 3: Introduction (Clip Art w/ Sound) Slide 4: Computer Virus Slide 5: How To Get A Virus Slide 6: Antivirus Software Slide 7: Protect Yourself
366 views • 15 slides

Internet security
Internet security. internet. What is it? Good Bad Ugly How our computers get sick Virus Malware AdWare RootKits. HACkers. Who are they Why do they ? What do they ? How do they ? Whitehat & Blackhat Popular folks: Kevin Mitnick , Vlad Levin, Ancheta. Security : Browsing.
716 views • 8 slides

Internet Security
Internet Security. Sunil Ji Garg GM, Software, UPTEC. Living in a World Of Hackers, Crackers, Thieves & Terrorists . Railway Tickets Fraud. Increase in site visits but decrease in business. Digit Site Redirected Internet British Lottery Fraud. Fake NASA Examination
378 views • 21 slides

Internet Security
Internet Security. Putting together the building blocks. Agenda. Basic cryptography Hash functions Secret key cryptography Public key cryptography Providing identity Verifying information Keeping secrets Key management Internet security protocols.
366 views • 14 slides

Internet Security
Internet Security. Internet Security. The Internet is connecting an estimated 820 million computers in 260 countries on every continent
508 views • 30 slides

Internet Security:
Internet Security:. Les Smee Georgia Tech Research Institute. Famous Hacking. John Draper Handle: Cap'n Crunch. Claim to fame:
434 views • 31 slides

Internet Security
Internet Security. What you need to know about Internet security. Do you have a computer? Whether it is connected to the internet or not, you and your computer can be at risk from a number of dangers.
367 views • 12 slides
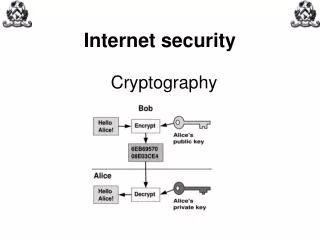
Internet security
Internet security. Cryptography. Cryptography. Cryptography is derived from the word ‘Kryptos’ which means hidden or secret. Cryptography. Cryptography is thought to date back to the Egyptians and their use of hieroglyphics. Cryptography. Hieroglyphics were complex pictograms.
441 views • 17 slides

Internet Security
Internet Security. Michael O’Farrell Ernst & Young 23-November-1999. Background. The Internet is increasingly used for commercial activities e.g. Information, Ordering, Payment.
474 views • 10 slides

Internet Security
Internet Security. Cyber Crime on the Rise 9-11 Points Out Our Vulnerability E-Commerce on the Rise! Fills a Gap in MCSE, Web Development & Programming Classes. Job Market for Students. American Express IBM Motorola Mayo Clinic State of Arizona Intel Discover.
135 views • 5 slides

Internet Security

Internet Security
Internet Security. Professor R A Carrasco School of Computing. Overview. Internet security is the practice of protecting and preserving private resources and information on the Internet.
344 views • 31 slides
























